Authenticate an API call
Every API endpoint that requires authentication expects anauthorization HTTP-header
with a signed JWT token as its value (prefixed with bearer).
Create an API key
To sign a JWT, create a new API key-pair in the dashboard. To create a new API key visit the Integrations panel in the dashboard and click the Add API key button. The API key can be stored with the code or in a secure environment accessible to the app.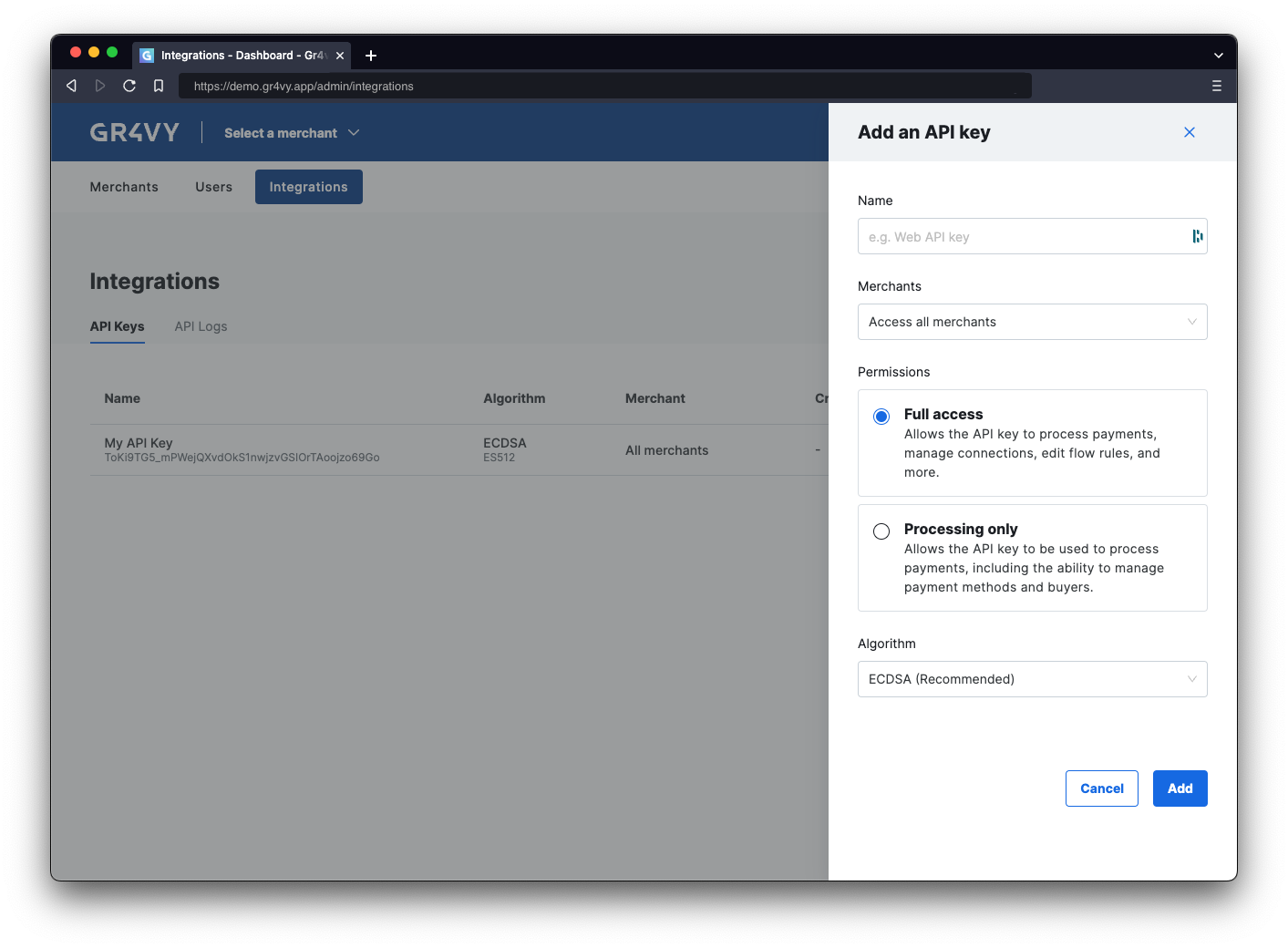
Merchants access
When selecting an API key, if the instance has Multi Merchant enabled then select whether the API key can access All merchants or only one. It is recommended to restrict an API key to only one merchant account when integrating into Embed, the SDKs, or the e-commerce platforms like Magento, Salesforce Commerce Cloud, and Commerce Tools.Permissions
When selecting an API key, select whether to generate a key that has access to all APIs within the merchants it has access to (Full access) or only to APIs used for processing payments (Processing only). It is recommended to use the Processing only for any API keys with the e-commerce platforms like Magento, Salesforce Commerce Cloud, and Commerce Tools.API access can be further reduced by setting a restrictive set of
scopes on the JWT.
Algorithm
The API supports 2 algorithms for signing JWTs, namely ECDSA and RSA. It is recommended to use ECDSA unless the environment does not support this stronger and newer algorithm. The RSA algorithm is available for those environments that do not support ECDSA. RSA keys provide considerably less security for the same key size and are currently not supported by the SDKs.Generate JWT
When not using one of the SDKs, or an SDK in the language is not available, construct and sign the JWT with one of the many libraries available onjwt.io.
At the high level a JWT is build up out of 3 pieces:
- A header defining the algorithm and key used to create the JWT.
- A set of claims that define the token’s scope and other permissions.
- A cryptographic signature based on the header and the claims, signed using the private key.
jwt.io for more details on the specification and available
libraries for generating JWTs.
JWT header
The JWT header defines the type of encryption algorithm as well as the private key used to generate the signature.The
typ and alg are fixed and do not allow for other values. The kid is
the ID of the private key, which can be found in the Integrations panel of
the dashboard.JWT claims
The claims define when the token was created and what access it has.Claims
The API supports the following JWT claims.| Description | Required | |
|---|---|---|
iss | A unique ID that represents your code making this call. This helps identify what library made a call to the API. | Yes |
nbf | The UNIX timestamp (in seconds) that this token was created at. | Yes |
exp | The UNIX timestamp (in seconds) that this token expires at. | Yes |
iat | An optional UNIX timestamp (in seconds) for your internal use to indicate when the token was issued. | No |
jti | A random unique ID used for cryptographic entropy. This needs to be unique for each JWT. | Yes |
scopes | A list of scopes that give this token access to the API. | Yes |
embed | A dictionary of key-value pairs used to pin the amount, currency, and buyer info for use in Embed. | No |
checkout_session_id | The ID of a checkout session. This can be used to tie multiple transactions together as having originated from the same session. | No |
TimestampsPlease be aware that the
nbf, exp, and iat values are UNIX timestamps defined as seconds since January 1, 1970 (UTC). Some programming languages return UNIX timestamps as milliseconds,
requiring the removal of the last three digits.Scopes
The API supports the following values for thescopes claims.
| Scope | Description |
|---|---|
*.read | Allows read-access to any resource. This is used by default in the SDKs |
*.write | Allows write-access to any resource. This is used by default in the SDKs. This does not also allow read access. |
{resource_name}.read | Allows read-access to a type or resource. For example, payment-services.read enabled read-access for buyers data. |
{resource_name}.write | Allows write-access to a type or resource. For example, payment-services.write enabled write-access for buyers data. This does not also allow read access. |
embed | A scope that represents all the access needed by Embed. |
anti-fraud-servicesapi-logsbuyersbuyers.billing-detailscard-scheme-definitionscheckout-sessionsconnectionsdigital-walletsflowspayment-methodspayment-method-definitionspayment-optionspayment-service-definitionspayment-servicesreportstransactions
Signature & assembly
Finally, the JWT signature is generated by appending the Base64 encoded header and claims (separated with a.) and run it through the key’s algorithm.